[DHCP Security]-prevention of Rogue DHCP with Bridge Filters
In the previous article we have discussed about DHCP Security for prevention against the presence of a DHCP Server or multiple DHCP Rogue. One example we can use the parameter "Authoritative" on the configuration of the DHCP Server. For more details can be seen at the link here.
However, in addition to the ways we can use another alternative that is by filtering traffic at layer 2 devices. Outline later Discover DHCP traffic from the client can only be done via a link where the DHCP Server is the "original" is connected. And another link will close the path to Discover DHCP traffic.
The DHCP Process
DHCP (Dynamic Host Configuration Protocol) is a protocol used to provide/distribution of IP Address to client devices on the network dynamically. In MikroTik itself can be enabled as DHCP Sever or DHCP Client.
To process its own transport protocol DHCP UDP (User Datagram Protocl) with port 67 (Server) and 68 (Client). If the DHCP process diagram is described as follows:
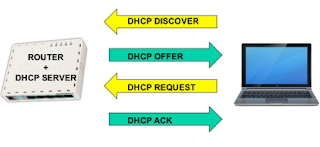
By knowing the process of how DHCP work above we can do filtering trafiknya to prevent the existence of another DHCP server that can interfere in the one network. In the example case, this time we will filter the DHCP traffic is the Discovery of the client.
Case + LAB
Examples of cases there is a network topology where in one/subnet/segment IP network there is a DHCP Server is active. Accidentally there was a another DHCP Server is active, so it is possible the Client will even get IP Address from DHCP Server Rogue. As a result of client connections become compromised, the client cannot access to the internet because the IP information is not appropriate. In this case, we're going to Discover DHCP traffic blocking it from the Client to the DHCP Server in addition to the original.
Like the above topology for filtering traffic we can utilize a MikroTik Router with bridge mode. From this bridge mode we can utilize the features of the bridge filters for handling big layer 2 communications that pass through the Arabian Ranches.
Let's say the topology is appropriate, the original DHCP Server connected on port ether1 MikroTik Bridge and DHCP client connected devices as well as Rogue on another port. Thus, we could make a rule to allow DHCP traffic (ACCEPT) Discover that past ether1 and doing blocking (DROP) in the ethernet port of the other.
We will focus on filtering settings on the menu at MikroTik Bridge Bridge--> Filters--> click Add [+]. Then we add to rule 2 that is the first rule to ACCEPT and rule both for the DROP. The rule is as follows:
/interface bridge filters
Add action = accept chain = forward dst-port = 67 ip-protocol = udp mac-protocol = ip out-interface = ether1 src-port = 68
Add action = drop chain = forward dst-port = 67 ip-protocol = udp mac-protocol = ip src-port = 68
If seen through winbox his rule as follows:
With the above rule when there is traffic from client (DHCP Discovery) with Src. Port 68 and Dst-Port, protocol UDP 67 out of ether1 will be on ACCEPT. In addition to the type of traffic the same outgoing interface in addition to ether1 will DROP in.
*) Note:
Rule ACCEPT make sure put currently top the most small/number.
However, in addition to the ways we can use another alternative that is by filtering traffic at layer 2 devices. Outline later Discover DHCP traffic from the client can only be done via a link where the DHCP Server is the "original" is connected. And another link will close the path to Discover DHCP traffic.
The DHCP Process
DHCP (Dynamic Host Configuration Protocol) is a protocol used to provide/distribution of IP Address to client devices on the network dynamically. In MikroTik itself can be enabled as DHCP Sever or DHCP Client.
To process its own transport protocol DHCP UDP (User Datagram Protocl) with port 67 (Server) and 68 (Client). If the DHCP process diagram is described as follows:

By knowing the process of how DHCP work above we can do filtering trafiknya to prevent the existence of another DHCP server that can interfere in the one network. In the example case, this time we will filter the DHCP traffic is the Discovery of the client.
Case + LAB
Examples of cases there is a network topology where in one/subnet/segment IP network there is a DHCP Server is active. Accidentally there was a another DHCP Server is active, so it is possible the Client will even get IP Address from DHCP Server Rogue. As a result of client connections become compromised, the client cannot access to the internet because the IP information is not appropriate. In this case, we're going to Discover DHCP traffic blocking it from the Client to the DHCP Server in addition to the original.
Like the above topology for filtering traffic we can utilize a MikroTik Router with bridge mode. From this bridge mode we can utilize the features of the bridge filters for handling big layer 2 communications that pass through the Arabian Ranches.
Let's say the topology is appropriate, the original DHCP Server connected on port ether1 MikroTik Bridge and DHCP client connected devices as well as Rogue on another port. Thus, we could make a rule to allow DHCP traffic (ACCEPT) Discover that past ether1 and doing blocking (DROP) in the ethernet port of the other.
We will focus on filtering settings on the menu at MikroTik Bridge Bridge--> Filters--> click Add [+]. Then we add to rule 2 that is the first rule to ACCEPT and rule both for the DROP. The rule is as follows:
/interface bridge filters
Add action = accept chain = forward dst-port = 67 ip-protocol = udp mac-protocol = ip out-interface = ether1 src-port = 68
Add action = drop chain = forward dst-port = 67 ip-protocol = udp mac-protocol = ip src-port = 68
If seen through winbox his rule as follows:
With the above rule when there is traffic from client (DHCP Discovery) with Src. Port 68 and Dst-Port, protocol UDP 67 out of ether1 will be on ACCEPT. In addition to the type of traffic the same outgoing interface in addition to ether1 will DROP in.
*) Note:
Rule ACCEPT make sure put currently top the most small/number.





Exellent!!! It works just fine!! Bocks remote DHCPs but not the local on the MT..
ReplyDelete